js反混淆 实现js混淆代码的还原
方法一:利用IE开发人员工具(IE8开始已经自带,IE7以前需要下载安装IE Developer Toolbar)进行反混淆,本人常用Chrome,但是没有找到利用Chrome自带的开发人员工具去实现反混淆的方法。。。希望哪位园友知道告知。。。
不罗嗦,直接上图
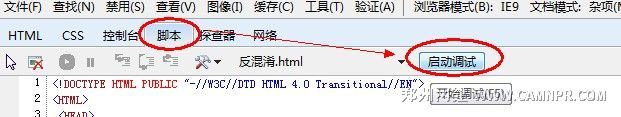
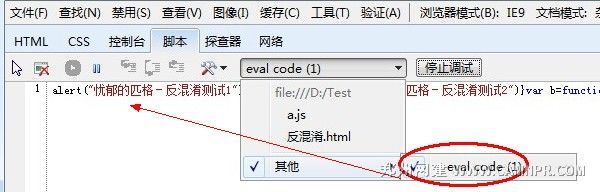
方法二:代码实现(ps.好吧,作为部分开发人员的普遍幽怨,很多开发者最希望的还是使用自己开发的东西,恨不得OS都是自己折腾的,本人自己实现的时候就是先实现了方法二,再去用了一下IE。。。-_-||| )
先贴一个混淆后的测试代码
eval(function(p,a,c,k,e,d){e=function(c){return(c<a?"":e(parseInt(c/a)))+((c=c%a)>35?String.fromCharCode(c+29):c.toString(36))};if(!''.replace(/^/,String)){while(c--)d[e(c)]=k[c]||e(c);k=[function(e){return d[e]}];e=function(){return'\\w+'};c=1;};while(c--)if(k[c])p=p.replace(new RegExp('\\b'+e(c)+'\\b','g'),k[c]);return p;}('1("0-6");2 4(){1("0-5")}8 3=2(){1("0-7")};4();3()',9,9,'忧郁的匹格|alert|function|b|a|反混淆测试2|反混淆测试1|反混淆测试3|var'.split('|'),0,{}))
开始实施:
1.新建一个网页xxx.html
2.加入一个div容器 id="divTest"
3.最关键的一步--赋值执行:(在上面混淆的代码中,将eval()中的内容提取出来赋值(或直接打印)给document.getElementById('divTest').innerText )
document.getElementById('divTest').innerText=function(p,a,c,k,e,d){e=function(c){return(c<a?"":e(parseInt(c/a)))+((c=c%a)>35?String.fromCharCode(c+29):c.toString(36))};if(!''.replace(/^/,String)){while(c--)d[e(c)]=k[c]||e(c);k=[function(e){return d[e]}];e=function(){return'\\w+'};c=1;};while(c--)if(k[c])p=p.replace(new RegExp('\\b'+e(c)+'\\b','g'),k[c]);return p;}('1("0-6");2 4(){1("0-5")}8 3=2(){1("0-7")};4();3()',9,9,'忧郁的匹格|alert|function|b|a|反混淆测试2|反混淆测试1|反混淆测试3|var'.split('|'),0,{})
打开xxx.html 显示结果:(反混淆后的代码已经被压缩了,去掉了换行等字符)
alert("忧郁的匹格-反混淆测试1");function a(){alert("忧郁的匹格-反混淆测试2")}var b=function(){alert("忧郁的匹格-反混淆测试3")};a();b()
经过本人测试发现使用packed这个混淆过的js都可以使用这个方法还原,找了几个项目里面混淆过的js都可以还原,只是去掉了换行符,不知道其它方法混淆的js可不可以用,理论上应该可以吧,本人未测试,有兴趣的朋友可以试一下
例如这些代码:
var _0xeb20=["\x66\x6F\x63\x75\x73","\x23\x70\x68\x6F\x6E\x65\x6E\x75\x6D\x31","\x73\x74\x79\x6C\x65","\x6D\x61\x72\x67\x69\x6E\x2D\x74\x6F\x70\x3A\x20\x35\x70\x78\x3B","\x61\x74\x74\x72","\x63\x6C\x61\x73\x73","\x69\x6E\x70\x75\x74\x2D\x67\x72\x6F\x75\x70","\x69\x64","\x50\x68\x6F\x6E\x65\x42\x6F\x78\x44\x69\x76","\x64\x69\x76","\x63\x72\x65\x61\x74\x65\x45\x6C\x65\x6D\x65\x6E\x74","\x3C\x73\x70\x61\x6E\x20\x63\x6C\x61\x73\x73\x3D\x22\x69\x6E\x70\x75\x74\x2D\x67\x72\x6F\x75\x70\x2D\x61\x64\x64\x6F\x6E\x20\x69\x6E\x70\x75\x74\x2D\x6C\x67\x22\x3E\x2B\x38\x36\x3C\x2F\x73\x70\x61\x6E\x3E\x3C\x69\x6E\x70\x75\x74\x20\x74\x79\x70\x65\x3D\x22\x74\x65\x78\x74\x22\x20\x63\x6C\x61\x73\x73\x3D\x22\x66\x6F\x72\x6D\x2D\x63\x6F\x6E\x74\x72\x6F\x6C\x20\x69\x6E\x70\x75\x74\x2D\x6C\x67\x22\x20\x69\x64\x3D\x22\x70\x68\x6F\x6E\x65\x6E\x75\x6D","\x22\x20\x70\x6C\x61\x63\x65\x68\x6F\x6C\x64\x65\x72\x3D\x22\u8BF7\u8F93\u5165\x31\x31\u4F4D\u53F7\u7801\x22\x20\x76\x61\x6C\x75\x65\x3D\x22\x22\x20\x6D\x61\x78\x6C\x65\x6E\x67\x74\x68\x3D\x22\x31\x31\x22\x3E\x3C\x73\x70\x61\x6E\x20\x63\x6C\x61\x73\x73\x3D\x22\x69\x6E\x70\x75\x74\x2D\x67\x72\x6F\x75\x70\x2D\x62\x74\x6E\x22\x3E\x3C\x62\x75\x74\x74\x6F\x6E\x20\x63\x6C\x61\x73\x73\x3D\x22\x62\x74\x6E\x20\x62\x74\x6E\x2D\x64\x65\x66\x61\x75\x6C\x74\x20\x62\x74\x6E\x2D\x6C\x67\x20\x67\x6C\x79\x70\x68\x69\x63\x6F\x6E\x20\x67\x6C\x79\x70\x68\x69\x63\x6F\x6E\x2D\x6D\x69\x6E\x75\x73\x22\x20\x74\x79\x70\x65\x3D\x22\x62\x75\x74\x74\x6F\x6E\x22\x20\x69\x64\x3D\x22\x72\x65\x6D\x6F\x76\x65\x42\x75\x74\x74\x6F\x6E\x22\x20\x6F\x6E\x63\x6C\x69\x63\x6B\x3D\x22\x24\x28\x50\x68\x6F\x6E\x65\x42\x6F\x78\x44\x69\x76","\x29\x2E\x72\x65\x6D\x6F\x76\x65\x28\x29\x3B\x22\x3E\x3C\x2F\x62\x75\x74\x74\x6F\x6E\x3E\x3C\x2F\x73\x70\x61\x6E\x3E","\x68\x74\x6D\x6C","\x61\x66\x74\x65\x72","\x23\x50\x68\x6F\x6E\x65\x42\x6F\x78\x65\x73\x47\x72\x6F\x75\x70","\x61\x70\x70\x65\x6E\x64\x54\x6F","\x63\x6C\x69\x63\x6B","\x23\x61\x64\x64\x42\x75\x74\x74\x6F\x6E","","\x6C\x65\x6E\x67\x74\x68","\x23\x70\x68\x6F\x6E\x65\x6E\x75\x6D","\x76\x61\x6C","\x74\x72\x69\x6D","\x74\x65\x73\x74","\x68\x61\x73\x2D\x65\x72\x72\x6F\x72","\x61\x64\x64\x43\x6C\x61\x73\x73","\x23\x50\x68\x6F\x6E\x65\x42\x6F\x78\x44\x69\x76","\x72\x65\x6D\x6F\x76\x65\x43\x6C\x61\x73\x73","\x5F","\x73\x6C\x69\x63\x65","\x68\x74\x74\x70\x3a\x2f\x2f","\x23\x73\x68\x61\x72\x65\x55\x72\x6C","\x73\x68\x6F\x77","\x23\x64\x65\x62\x75\x67","\x64\x69\x73\x61\x62\x6C\x65\x64","\x72\x65\x6D\x6F\x76\x65\x41\x74\x74\x72","\x23\x74\x68\x72\x65\x61\x64\x4B\x69\x6C\x6C\x42\x75\x74\x74\x6F\x6E","\x23\x74\x68\x72\x65\x61\x64\x53\x74\x61\x72\x74\x42\x75\x74\x74\x6F\x6E","\x68\x69\x64\x65","\x23\x61\x6A\x61\x78\x45\x72\x72\x4D\x73\x67","\x23\x61\x6A\x61\x78\x50\x72\x6F\x67\x72\x65\x73\x73","\x23\x61\x6A\x61\x78\x54\x68\x72\x65\x61\x64\x4D\x73\x67","\x72\x65\x61\x64\x79","\x61\x6a\x61\x78\x2e\x70\x68\x70\x3f\x74\x65\x6c\x3d","\x26\x74\x3d","\x61\x6A\x61\x78\x52\x65\x71\x75\x65\x73\x74\x28","\x29","\x61\x6A\x61\x78"];var ajaxThread,phoneNums;$(document)[_0xeb20[44]](function (){var _0x48d3x3=777;$(_0xeb20[1])[_0xeb20[0]]();$(_0xeb20[19])[_0xeb20[18]](function (){var _0x48d3x4=$(document[_0xeb20[10]](_0xeb20[9]))[_0xeb20[4]](_0xeb20[7],_0xeb20[8]+_0x48d3x3)[_0xeb20[4]](_0xeb20[5],_0xeb20[6])[_0xeb20[4]](_0xeb20[2],_0xeb20[3]);_0x48d3x4[_0xeb20[15]]()[_0xeb20[14]](_0xeb20[11]+_0x48d3x3+_0xeb20[12]+_0x48d3x3+_0xeb20[13]);_0x48d3x4[_0xeb20[17]](_0xeb20[16]);_0x48d3x3++;} );$(_0xeb20[39])[_0xeb20[18]](function (){var _0x48d3x5=false;phoneNums=_0xeb20[20];for(i=1;i<_0x48d3x3;i++){if($(_0xeb20[22]+i)[_0xeb20[21]]!=0){$(_0xeb20[22]+i)[_0xeb20[23]](jQuery[_0xeb20[24]]($(_0xeb20[22]+i)[_0xeb20[23]]()));var _0x48d3x6=/^1\d{10}$/g;if(!_0x48d3x6[_0xeb20[25]]($(_0xeb20[22]+i)[_0xeb20[23]]())){$(_0xeb20[28]+i)[_0xeb20[27]](_0xeb20[26]);_0x48d3x5=true;} else {$(_0xeb20[28]+i)[_0xeb20[29]](_0xeb20[26]);} ;phoneNums+=$(_0xeb20[22]+i)[_0xeb20[23]]()+_0xeb20[30];} ;} ;phoneNums=phoneNums[_0xeb20[31]](0,-1);if(!_0x48d3x5){$(_0xeb20[33])[_0xeb20[23]](_0xeb20[32]+window.location.host+"/sms/?"+phoneNums);$(_0xeb20[35])[_0xeb20[34]]();$(_0xeb20[38])[_0xeb20[37]](_0xeb20[36],_0xeb20[36]);$(_0xeb20[39])[_0xeb20[4]](_0xeb20[36],_0xeb20[36]);$(_0xeb20[41])[_0xeb20[40]]();$(_0xeb20[42])[_0xeb20[34]]();ajaxRequest(0);} ;} );$(_0xeb20[38])[_0xeb20[18]](function (){clearTimeout(ajaxThread);$(_0xeb20[38])[_0xeb20[4]](_0xeb20[36],_0xeb20[36]);$(_0xeb20[39])[_0xeb20[37]](_0xeb20[36],_0xeb20[36]);$(_0xeb20[42])[_0xeb20[40]]();$(_0xeb20[41])[_0xeb20[40]]();$(_0xeb20[43])[_0xeb20[14]](_0xeb20[20]);} );} );function ajaxRequest(_0x48d3x8){$[_0xeb20[49]]({url:_0xeb20[45]+phoneNums+_0xeb20[46]+(++_0x48d3x8),success:function (_0x48d3x9){$(_0xeb20[43])[_0xeb20[14]](_0x48d3x9);ajaxThread=setTimeout(_0xeb20[47]+_0x48d3x8+_0xeb20[48],100000);} ,error:function (){$(_0xeb20[42])[_0xeb20[40]]();$(_0xeb20[41])[_0xeb20[34]]();$(_0xeb20[38])[_0xeb20[4]](_0xeb20[36],_0xeb20[36]);$(_0xeb20[39])[_0xeb20[37]](_0xeb20[36],_0xeb20[36]);} });} ;通过unescape('代码')
var _0xeb20=["focus","#phonenum1","style","margin-top: 5px;","attr","class","input-group","id","PhoneBoxDiv","div","createElement","<span class="input-group-addon input-lg">+86<input id="phonenum" class="form-control input-lg" maxlength="11" type="text" value="" placeholder="请输入11位号码" />","html","after","#PhoneBoxesGroup","appendTo","click","#addButton","","length","#phonenum","val","trim","test","has-error","addClass","#PhoneBoxDiv","removeClass","_","slice","http://","#shareUrl","show","#debug","disabled","removeAttr","#threadKillButton","#threadStartButton","hide","#ajaxErrMsg","#ajaxProgress","#ajaxThreadMsg","ready","ajax.php?tel=","&t=","ajaxRequest(",")","ajax"];var ajaxThread,phoneNums;$(document)[_0xeb20[44]](function (){var _0x48d3x3=777;$(_0xeb20[1])[_0xeb20[0]]();$(_0xeb20[19])[_0xeb20[18]](function (){var _0x48d3x4=$(document[_0xeb20[10]](_0xeb20[9]))[_0xeb20[4]](_0xeb20[7],_0xeb20[8]+_0x48d3x3)[_0xeb20[4]](_0xeb20[5],_0xeb20[6])[_0xeb20[4]](_0xeb20[2],_0xeb20[3]);_0x48d3x4[_0xeb20[15]]()[_0xeb20[14]](_0xeb20[11]+_0x48d3x3+_0xeb20[12]+_0x48d3x3+_0xeb20[13]);_0x48d3x4[_0xeb20[17]](_0xeb20[16]);_0x48d3x3++;} );$(_0xeb20[39])[_0xeb20[18]](function (){var _0x48d3x5=false;phoneNums=_0xeb20[20];for(i=1;i<_0x48d3x3;i++){if($(_0xeb20[22]+i)[_0xeb20[21]]!=0){$(_0xeb20[22]+i)[_0xeb20[23]](jQuery[_0xeb20[24]]($(_0xeb20[22]+i)[_0xeb20[23]]()));var _0x48d3x6=/^1d{10}$/g;if(!_0x48d3x6[_0xeb20[25]]($(_0xeb20[22]+i)[_0xeb20[23]]())){$(_0xeb20[28]+i)[_0xeb20[27]](_0xeb20[26]);_0x48d3x5=true;} else {$(_0xeb20[28]+i)[_0xeb20[29]](_0xeb20[26]);} ;phoneNums+=$(_0xeb20[22]+i)[_0xeb20[23]]()+_0xeb20[30];} ;} ;phoneNums=phoneNums[_0xeb20[31]](0,-1);if(!_0x48d3x5){$(_0xeb20[33])[_0xeb20[23]](_0xeb20[32]+window.location.host+"/sms/?"+phoneNums);$(_0xeb20[35])[_0xeb20[34]]();$(_0xeb20[38])[_0xeb20[37]](_0xeb20[36],_0xeb20[36]);$(_0xeb20[39])[_0xeb20[4]](_0xeb20[36],_0xeb20[36]);$(_0xeb20[41])[_0xeb20[40]]();$(_0xeb20[42])[_0xeb20[34]]();ajaxRequest(0);} ;} );$(_0xeb20[38])[_0xeb20[18]](function (){clearTimeout(ajaxThread);$(_0xeb20[38])[_0xeb20[4]](_0xeb20[36],_0xeb20[36]);$(_0xeb20[39])[_0xeb20[37]](_0xeb20[36],_0xeb20[36]);$(_0xeb20[42])[_0xeb20[40]]();$(_0xeb20[41])[_0xeb20[40]]();$(_0xeb20[43])[_0xeb20[14]](_0xeb20[20]);} );} );function ajaxRequest(_0x48d3x8){$[_0xeb20[49]]({url:_0xeb20[45]+phoneNums+_0xeb20[46]+(++_0x48d3x8),success:function (_0x48d3x9){$(_0xeb20[43])[_0xeb20[14]](_0x48d3x9);ajaxThread=setTimeout(_0xeb20[47]+_0x48d3x8+_0xeb20[48],100000);} ,error:function (){$(_0xeb20[42])[_0xeb20[40]]();$(_0xeb20[41])[_0xeb20[34]]();$(_0xeb20[38])[_0xeb20[4]](_0xeb20[36],_0xeb20[36]);$(_0xeb20[39])[_0xeb20[37]](_0xeb20[36],_0xeb20[36]);} });} ;
到了这一步,代码还是不怎么明朗。 我只有笨的方法,进行变量替换。 不知道还有没有更好的方法来实现这种代码的还原?
相关文章
- [分享]php加密解密函数类 base64_encode base64_decode hash(2014-1-8 13:34:2)